
Telegram Messenger is a communication app that allows you to create encrypted chats and phone calls with other users over the Internet. This program describes itself as being a secure and private communication app, but a researcher has shown that in its default configuration it would allow a user's IP address to be leaked when making call.
This is caused by a default setting in Telegram, which causes voice calls to be made over P2P. When using P2P to initiate Telegram calls, though, the IP address of the person you are speaking with will appear in the Telegram console logs. Not all versions include a console log. For example, Windows does not display a console log in our tests, while the Linux version does.
The Telegram app does indicate that users can prevent their IP address from being revealed by changing the setting at Settings -> Private and Security -> Voice Calls -> Peer-To-Peer to Never or Nobody. Doing this will cause the user's calls to be routed through Telegram's servers, which would then hide the IP address, but at the cost of having a slight decrease in audio quality.
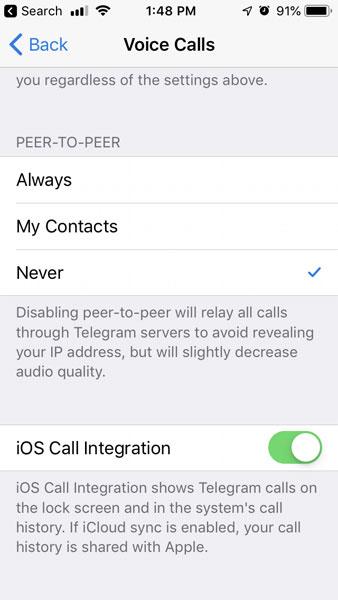
The problem is that while you are able to disable P2P calls and the associated IP address leak in iOS and Android, security researcher Dhiraj has discovered that the official Telegram for Desktop (tdesktop) and Telegram Messenger for Windows applications did not offer the ability to disable P2P calls.
This meant that these user's IP addresses would be leaked whenever they used Telegram to make a call. You can see an example of an IP address being leaked in the console for Telegram for Desktop on Ubuntu.
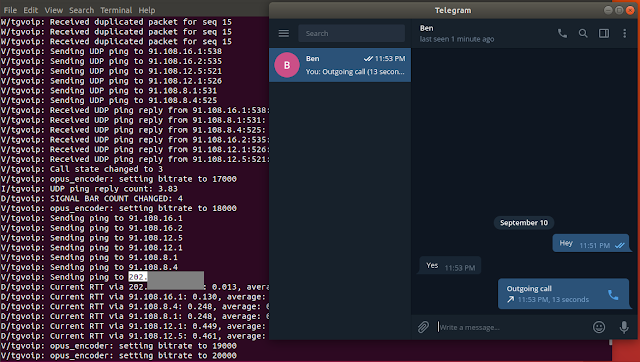
In conversations with Dhiraj, the researcher shared a Proof of Concept video with BleepingComputer that illustrated how the IP addresses were leaked.
"If you see in my video PoC there are 3 IP's that leak: 1. Telegram server IP (That's Ok) 2. Your own IP (Even that's okay too) 3. End user IP (That's not okay)" Dhiraj explained.
After alerting Telegram about this missing setting in Telegram for Desktop and Telegram for Windows, Dhiraj was awarded a €2,000 bounty and his report was assigned the CVE-2018-17780 ID.
This issue has since been fixed in the 1.3.17 beta and 1.4.0 versions of Telegram for Desktop, which have had a setting to disable P2P calls added to the program.
Why Telegram, an application that prides itself on security and privacy, would enabled P2P calling by default when they know it could leak IP addresses does not make sense. When BleepingComputer asked Dhiraj if Telegram had a reason for doing this, he told us "Nope, no comments on this was provided."
Update 9/30/18 2:36 PM EST: When we were the first to report this story, Telegram stated that the "My Contacts" option was the default Peer-To-Peer setting and that only a user's contacts would therefore see IP addresses. When I tested installing the app and setting it up for the first time, this setting would always default to the "Always" setting.
As stated in the previous thread. Sorry, something not right here.https://t.co/g0JblyYNWe
— Lawrence Abrams (@LawrenceAbrams) September 29, 2018
After further testing with BleepingComputer and other testers, the Telegram developers found a bug that would cause the app to use the Everyone or Always setting for a few hours and thus their IP addresses would be revealed by default.
The Telegram developer's description of the bug is below:
"We’ve found and fixed the issue which our tester had. It turns out that during the sign in process, the API returned no value for the option (treated as “everyone”). Then immediately after the user was signed in, the api returned the correct default value (my contacts). But it could take up to several hours for the client to refresh this configuration. So before we fixed this, the apps could display “everyone” in the settings for an hour or two after a fresh login."



Comments
tjhorner - 5 years ago
The title's a bit misleading - by default, the setting is "My Contacts", not "Always", so not everyone will see your IP, only those whose numbers you have saved. The bug was only present in Telegram Desktop (and as stated in the article, was very swiftly fixed).
Lawrence Abrams - 5 years ago
Tested from multiple phones. Each time Voice Calls -> Peer-To-Peer was set to Always. Telegram needs to clarify this. I already sent them info.